Reaver vs Netgear DGN2200
by skullkey

The guys from Tactical Network Solutions released an open source project called reaver that implements an attack on WPA http://code.google.com/p/reaver-wps/ using WPS.
“Reaver implements a brute force attack against Wifi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases, as described in http://sviehb.files.wordpress.com/2011/12/viehboeck_wps.pdf”
I tested this against my home router a Netgear DGN2200 using my eee-pc with an Atheros wireless chipset and the FOSS ath5k driver.

After tweaking the command line parameters a bit, I managed to crack the password in 7 hours 45 minutes.
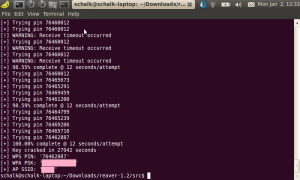
Lessons learnt:
1. It is all about hardware / drivers – tried using other hardware – about three times slower using HP laptop with Intel chipset
2. Tweaking the command line helps a lot, in this case the delay between attempts and the way it handles AP lock outs
Next step
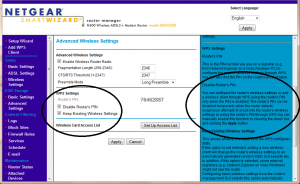
The WPS feature can be disabled in the Netgear control panel – I disabled WPS and am running reaver against it again
Update
Netgear FAIL – when you turn-off the WPS pin, it only slows down the brute force attack, but does not prevent it. It took 30 hours to crack.
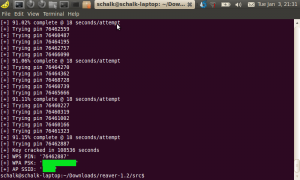
The guys from Tactical Network Solutions released an open source project called reaver that implements an attack on WPA http://code.google.com/p/reaver-wps/ using WPS. “Reaver implements a brute force attack against Wifi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases, as described in http://sviehb.files.wordpress.com/2011/12/viehboeck_wps.pdf” I tested this against my home router a Netgear DGN2200…
2 Comments
Leave a Reply Cancel reply
You must be logged in to post a comment.
Get involved
Visit us on a Tuesday:
- Join us at 4 Burger Ave, Lyttleton Manor, Centurion every Tuesday evening from 18.00 till late (bring a project to work on or beer)
Telegram Group:
- Send a message to Schalk on Telegram to add you to the group - currently >100 users, relevant conversations for makers
IRL:
- Schalk 082 777 7098
After hours only, please rather send telegram message - Toby
http://tobykurien.com
- Not active at the moment, if you are interested in presenting a course, please let Schalk know

Hi,
Do you mind sharing what tweaks you used in order to make reaver work?
Have you ever ran across an issue where it was getting stuck at ‘Sending EAPOL START request’ and timing out?
Cheers,
m